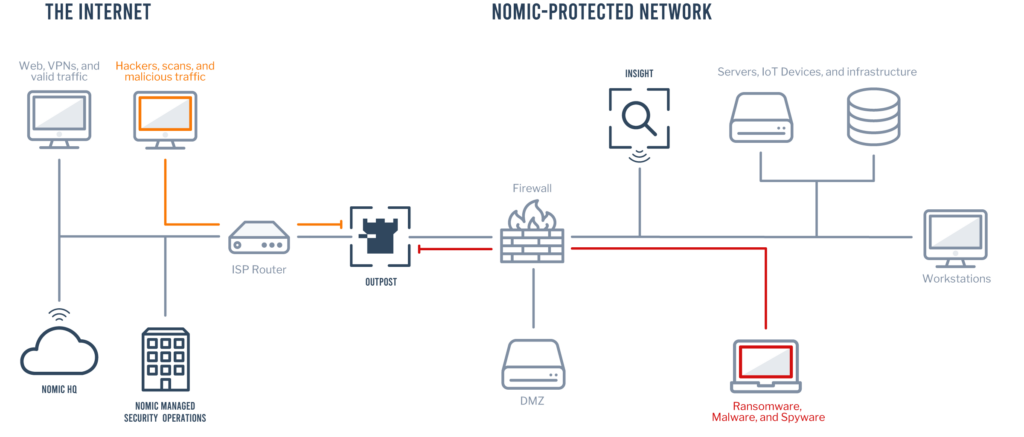
It's like adding to your security team, without adding overhead.
Managed Security Operations
With Nomic, you don’t just get a comprehensive network security solution, but a team of seasoned security experts looking out for you—monitoring critical alerts, researching new threats, and troubleshooting issues, 24/7, 365 days a year. When you need support, there’s a real, live person waiting to help, anytime, day or night. When you don’t, you can rest assured that there’s an extra set of eyes watching over your network.
So, you can get back to all of the other things on your to-do list, and maybe even sleep a little better at night. That’s easier to do when someone has your back. And we do.