GENERAL
Apis And Protocols: What You Need To Know
An Application Programming Interface (API) is a set of definitions and protocols for building and integrating application software. APIs let your product or service communicate with other products and services without having to know how they’re implemented.
API is an interface in which applications communicate with each other through programs that are defined as a set of functions and rules with specific instructions as to how communication should take place.
How do APIs work?
As stated previously, APIs exist where there is a need for communication between two or more applications. This communication thus requires one of the applications to initiate an interaction that comes in the form of a Request. The request is followed by a Response from the receiving application after a Program is run. The entirety of this interaction is called an API transaction or contract and this can happen with or without web access.
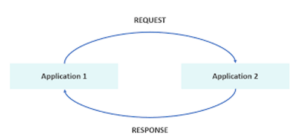
The above definition only covers how APIs work from a foundational perspective. The various types and protocols available for APIs offer a more robust definition of how APIs work by shedding more light on each type and protocol.
Why APIs?
APIs revolutionized the way applications communicate with each other by drastically enhancing connectivity while also aiding developers in building and deploying applications. This invariably introduced a new era of seamless software integration either using originally built API tools or pre-built software that offer API integrations as some form of platform-as-a-service. While the advantages of using APIs are numerous, they broadly can be grouped under improved automation, enhanced customer experiences, improved software connectivity, and collaboration, increased efficiency and adaptation, and seamless integration of software.
Types of APIs
The ‘type’ classification of APIs is specific to APIs used in web applications, of which there are four (4) principal types: public, partner, private and composite.
It is important to note that each API “type” is an indicator of the intended scope of use.
- Public APIs: Public APIs are developed mainly by businesses who intend to make their applications and data public. To do this, a public API is made open source and available for use by just about anyone who wants to use them. Public APIs usually involve minimal Identity Access Management. Profit can also be generated from Public APIs by using a per-call cost for anyone looking to use the public API.
- Partner APIs: As the name implies, partner APIs are authorization-specific APIs that are only available to a select few. They are used mainly to facilitate business-to-business activities with partners having licences and rights to use the API. They are much more secure than public APIs as they require the incorporation of stronger authorization, authentication, and overall security mechanisms. Profit is generated through paid subscriptions from partners as against a per-cost call utilization.
- Private APIs: Private APIs are often called internal APIs and are used within an enterprise environment for interaction between systems and data. From a security perspective, Internal APIs offer no or weak security and authentication, often leveraging a more robust security network in use within the enterprise environment. With greater awareness and a better focus on API security, alongside regulatory compliance demands, companies are adopting better security strategies for APIs.
- Composite APIs: Composite APIs are a combination of multiple (two or more) APIs crafted together in sequential requests to form a single API call. Rather than have multiple API calls running individually, composite APIs come into place to address complex API behaviours and improve the speed and performance of individual APIs.
API Protocols
To cater to the complex data and commands exchanged by APIs, clear-cut protocols and architectures that govern API operations are necessary. Each of these protocols is employed differently and has its unique characteristics.
Overall, there are three categories of API protocols; REST, SOAP, and RPC.
REST: REST which stands for Representational State Transfer is a stateless and flexible API that relies on a client/server approach to separate front and back ends during its call. It is the most widely used of all the APIs, comprising approximately 70% of all public APIs. REST supports caching which stores responses for slow or non-time-sensitive APIs. REST APIs are majorly used to gain access to web resources, returning data in formatted languages such as HTML, XML, or JSON.
REST utilizes a set of methods available to HTTP to carry out operations. The most popular of these methods are GET, POST, PUT and DELETE.
A REST API request comprises four parts; URI, HTTP method, headers, and response.
REST APIs are flexible in nature and communicate directly through intermediate systems such as API gateways and load balancers.
SOAP: The SOAP (Simple Object Access Protocol) API protocol can be used to create, get, update, or remove records like accounts, leads, and user-defined objects. It is highly structured, strictly regulated, and well outlined. You can use the SOAP API in any language that supports web services to manage passwords, conduct searches, etc. with more than 20 distinct methods.
The payload of a SOAP API can have up to four components, including an envelope, a header, a body, and a fault (error handling), making them more complex than REST API.
RPC: Remote Procedure Call is the earliest and most basic type of API interaction that involves running a section of code on a different server, and when done via HTTP or AMQP, it can function as a Web API. There are some arguments and a procedure, but that is about it. Consider it similar to executing a JavaScript function that accepts a method name and parameters.
When compared to REST APIs which primarily exchange data or resources, RPC can also make use of JSON and XML, referred to as JSON-RPC and XML-RPC respectively, for its API calls.
It is noteworthy that Browser and IOS/Android APIs are also used. While browser APIs are used for a wide variety of user experiences on browsers by using JavaScript to manipulate HTML, IOS/Android APIs allow developers to build experiences for their end users through APIs that interact with device hardware in various capabilities.
Conclusion
APIs have served as the foundational building blocks for the way systems communicate over the internet in the past two decades, allowing developers to build more complex applications that can easily communicate with each other, sharing sensitive information and data in the process. APIs have grown in popularity, with a 26% increase in businesses using twice as many APIs as the previous year and an overall API traffic growth of 321%. This has invariably led to APIs becoming the primary attack vector for Cyber Criminals with research showing that 95% of a particular demography of companies have had an API security incident over the past 12 months, representing a 681% increase in API attack traffic.
Simply put, API security is as important as picking the most suitable API protocol. API security ensures data being transmitted is protected, user experience is not affected and compliance and regulatory standards are met.
Musa Nadir is a certified Cybersecurity Analyst and Technical writer. He has experience working as a Security Operations Center (SOC) Analyst and Cyber Threat Intelligence Analyst (CTI) with a history of writing relevant cybersecurity content for organizations and spreading best security practices. He is a regular writer at Bora.
His other interests are Aviation, History, DevOps with Web3 and DevSecOps. In his free time, he enjoys burying himself in a book, watching anime, aviation documentaries and sports, and playing video games.
Put Us In Your Corner.
We back you up with managed threat protection, visibility, and support, 24/7.